Did you know that phishing increases during a crisis like the current pandemic? And even before the pandemic, phishing was a major cybercrime threat.
Cybercriminals keep upping their game, making the problem more difficult to detect. According to Anti-Phishing Working Group, as of the third quarter of 2020, 80 percent of phishing sites used SSL encryption (HTTPS) in their Web address (APWG Trends Report). Gone are the days when you could look for “HTTPS” in the URL and be sure the site could be trusted.
Because cybercrime keeps evolving, it’s more important than ever for your bank to teach your employees how to spot phishing attempts, including the latest trends.
In our last blog, we gave an overview of some important ways your bank can prevent cybercrime.
In this article, we’ll give you four strategies for identifying phishing attempts and preventing them from succeeding:
- Study real-world examples of phishing attempts.
- Examine everything in emails that ask you to respond.
- Confirm with colleagues.
- Think before you act.
Let’s get started.
1. Study real-world examples of phishing attempts.
One good way to learn how to spot phishing attempts is to analyze real-world examples. As mentioned earlier, pandemic-related phishing attempts have emerged in the last year, so we’ll look at some examples of those to help you stay current.
Phishing attacks rely on a sense of urgency to entice people to react quickly, and crises like the current pandemic make victims more likely to take the bait. When people are already on edge, they’re eager for new information from apparent authorities like employers and the government. An email that seems to have been sent by a trusted entity that offers information or creates a heightened sense of urgency to act fast can easily take advantage of a recipient’s anxieties.
With more people working remotely now, criminals can exploit the common use of Microsoft OneDrive to share files among remote workers. The following phishing email is an actual example of one such phishing attempt.
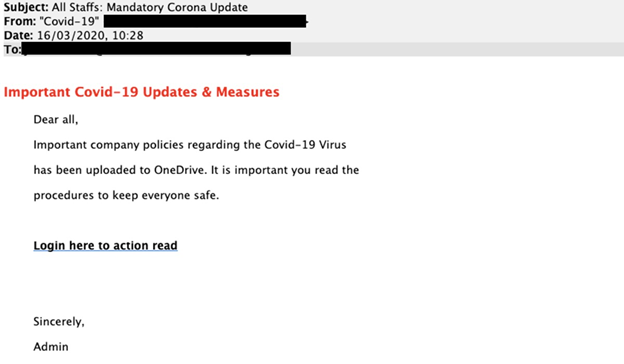
This example is insidious because there aren’t any obvious clues of fakery, such as misspellings or odd word usage, in the body of the email. But there are hints in the rest of the message. Did you notice the header? Probably not, because most readers skip the header. The “To:” line is addressed to “All Staffs.” Sounds odd, doesn’t it? The word “staff” used in this context is almost always singular in standard English usage.
The greeting “Dear all” is also unusual in standard U.S. English; we’d expect something like “Dear employees” or “To all employees.” One other subtle clue is the use of “Admin” as the signature. In most cases, an actual employee of your company would sign their name. These hints would likely be overlooked by most recipients, which is one reason such emails succeed.
Two other recent examples of pandemic phishing campaigns were identified by Proofpoint, an enterprise security company. One asks recipients to install an app on their device to "run simulations of the cure" for COVID-19. The app, of course, is malware. A second seems to be from Canada's Public Health Agency and asks victims to click on a link to read an important letter. The link goes to a malicious document.
Here’s another real example:
FROM: John (abuse@gradcad.com)
SUBJECT LINE: The following is a safe message from Humana
Hello there,
The following invoice statement message is delivered to you by Humana.
Thanks for your recent order of Coronavirus (COVID-19) insurance plan.
Kindly follow the link down below to see invoice statement.
Do you see any clues in this email that it’s not legitimate? Of course, if you didn’t order a Coronavirus insurance plan, that’s a red flag. Also look closely at the “From:” line, which shows “John (abuse@gradcad.com).” If this email had actually been sent from Humana, it would show Humana’s email address.
For more real examples of phishing emails, see a website maintained by Lehigh University's technology services department where they keep a gallery of phishing emails received by students and staff.
2. Examine everything in emails that ask you to respond.
As the previous examples illustrate, it’s important to look closely at any email you receive that asks you for a response action: to open an attachment, click on a link, download something, or send any personal information.
Closely examine the sender’s name and email address. For example, suppose you receive an email that seems to be from “Amazon Best Sellers.” To determine whether the sender truly is Amazon, look at the actual email address and domain name. If it’s a phishing attempt, you’ll see something that doesn’t fit (for example: Email name: Amazon.Best.Sellers. Email domain: @happyvalleydental.com).
If the sender asks you to click on a link, beware: do not click it before you investigate it. Hover your cursor over the link, and you’ll see the Web address the link is connected to. However, even if it seems legitimate, it may not be. Sometimes a fake website will have almost the same URL as the real website it’s imitating. If you have any doubt, don’t click on the link.
3. Confirm with colleagues.
Some phishing emails are sophisticated enough to seem like they were sent by your work colleagues, including the name of a coworker. The best way to prevent falling for a phishing scam that seems to come from an internal sender is to follow this rule: If you don't know, ask. Call that coworker to confirm that they actually did send you a request for information.
Below is an actual example of a phishing attempt (with the names changed for security reasons). This email included the actual names of the two employees in the From: and To: lines.
From: Martha Washington <ceo@ABCBank.com>
Sent: Friday, April 5, 2019 9:24 AM
To: Abigail Adams <aadams@FPSGOLDBank.com>
Subject: Abigail Adams
Are you available now? I want you to assist me in handling something.
Reach me here via email (ONLY). Am going into a long meeting right now.
Martha Washington
President/CEO
FPS GOLD Bank
Sent from my iPad
If you were Abby Adams and received this email that seemed to be from your CEO, what would you do? Phishing scams like this are particularly dangerous because, even if you did suspect foul play, you might be too afraid to confront your boss or seem to ignore the urgent request.
What’s the clue here? The only clues in this case are the sense of urgency and “via email (ONLY).” The scammer wants to trick you into reacting fast and not asking for confirmation from the CEO.
However, organizations that value cyber security would accept that it’s better to be safe than sorry and perhaps even congratulate you if you checked with the CEO instead of replying to this email.
4. Think before you act.
Whenever you receive an email with an attachment, a link, an unusual sense of urgency, or a request for sensitive information like an account number, pause to think before taking action. Be especially skeptical if the message uses high-pressure sales tactics. Scammers count on making you act before you think, and they know common emotional triggers.
Education Is Key
The previous examples make it clear that scammers are hard at work creating improved ways to cheat your bank. Ongoing training to teach employees how to identify phishing emails is key to defending against attacks. Make sure they know not only how to spot a suspicious email, but also what to do about it, such as:
- Don’t open any email, click on any links, or download/open any attachments unless you’re sure the email is legitimate.
- Report any suspicious email to your IT security team.
- Follow organizational security policies.
How do you know if everyone in your bank has understood and internalized the training? One good way is to test them by sending mocked-up phishing emails to everyone in the company, like the one below.
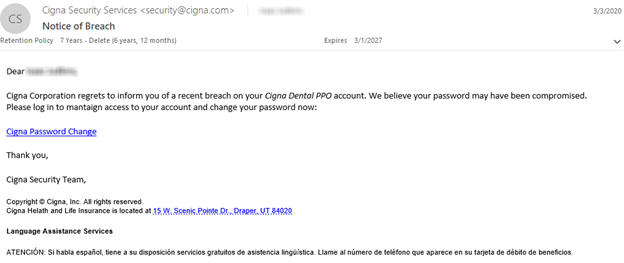
In the example above, the actual name of each recipient was spelled correctly, and the company dental plan is handled by Cigna.
Can you see any clues that this is a phishing attempt? There’s one misspelled word, which many people would miss: “maintaign.” Everything else seems to be in order. The key here is to drive home this point in training: be suspicious of links in emails. This email also plays on a sense of urgency. The only completely safe way to find out if there’s a legitimate risk to your account is to look up the phone number of the company and call them.
If you send test emails like the one above to the entire company and see that many employees are taking the bait, you know it’s time for more training.
There are, of course, many companies that offer such training and other security measures for a fee. Only you can determine whether your budget and needs warrant hiring a service for this purpose. There’s also a great deal of information offered for free on the Internet. Look for recent articles from trusted sources. Here are a couple of helpful resources for more information:
- “How to Recognize and Avoid Phishing Scams” (FTC government website): https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
- “What is phishing? How this cyber attack works and how to prevent it” (from CSO, an online cybersecurity magazine): https://www.csoonline.com/article/2117843/what-is-phishing-how-this-cyber-attack-works-and-how-to-prevent-it.html
You can also place posters on walls at your workplace to remind employees to be alert. Many good posters are available online for free download.
Conclusion
It requires vigilance to stay ahead of the scammers. Unfortunately, many phishing attempts succeed, which gives criminals continued incentive to keep trying. Your investment of time (and, if you think it necessary, money) to educate yourself and others at your bank will be well rewarded.

